
[ad_1]

|
Amazon S3 turned 15 earlier this yr, and Amazon EC2 will do the identical in a few months. Right now we’re celebrating the tenth birthday of AWS Identification and Entry Administration (IAM).
The First Decade
Let’s take a stroll by means of the final decade and revisit a number of the most important IAM launches:
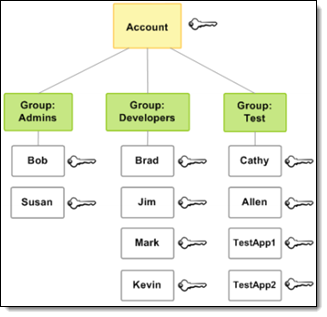 Could 2011 – We launched IAM, with the power to create customers, teams of customers, and to connect coverage paperwork to both one, with help for fifteen AWS companies. The AWS Coverage Generator might be used to construct insurance policies from scratch, and there was additionally a modest assortment of predefined coverage templates. This launch set the usual for IAM, with fine-grained permissions for actions and sources, and the usage of circumstances to manage when a coverage is in impact. This mannequin has scaled together with AWS, and stays central to IAM at present.
Could 2011 – We launched IAM, with the power to create customers, teams of customers, and to connect coverage paperwork to both one, with help for fifteen AWS companies. The AWS Coverage Generator might be used to construct insurance policies from scratch, and there was additionally a modest assortment of predefined coverage templates. This launch set the usual for IAM, with fine-grained permissions for actions and sources, and the usage of circumstances to manage when a coverage is in impact. This mannequin has scaled together with AWS, and stays central to IAM at present.
August 2011 – We launched the power so that you can use current identities by federating into your AWS Account, together with help for short-term short-term AWS credentials.
June 2012 – With the introduction of IAM Roles for EC2 cases, we made it simpler for code working on an EC2 occasion to make calls to AWS companies.
February 2015 – We launched Managed Insurance policies, and concurrently turned the present IAM insurance policies into first-class objects that might be created, named, and used for a number of IAM customers, teams, or roles.
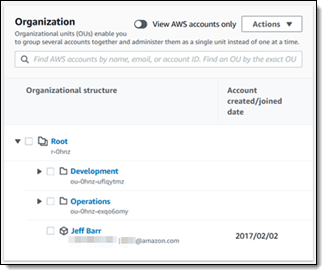 February 2017 – We launched AWS Organizations, and gave you the power to to implement policy-based administration that spanned a number of AWS accounts, grouped right into a hierarchy of Organizational Models. This launch additionally marked the debut of Service Management Insurance policies (SCPs) that gave you the facility to put guard rails across the degree of entry allowed throughout the accounts of an Group.
February 2017 – We launched AWS Organizations, and gave you the power to to implement policy-based administration that spanned a number of AWS accounts, grouped right into a hierarchy of Organizational Models. This launch additionally marked the debut of Service Management Insurance policies (SCPs) that gave you the facility to put guard rails across the degree of entry allowed throughout the accounts of an Group.
April 2017 – Constructing on the IAM Roles for EC2 Cases, we launched service-linked roles. This gave you the facility to delegate permissions to AWS companies, and made it simpler so that you can work with AWS companies that wanted to name different AWS companies in your behalf.
December 2017 – We launched AWS Single Signal-On to make it simpler so that you can centrally handle entry to AWS accounts and your corporation purposes. SSO is constructed on prime of IAM and takes benefit of roles, short-term credentials, and different foundational IAM options.
November 2018 – We launched Attribute-Primarily based Entry Management (ABAC) as a complement to the unique Function-Primarily based Entry Management to permit you to use varied varieties of person, useful resource, and surroundings attributes to drive coverage & permission choices. This launch allowed you to tag IAM customers and roles, which allowed you to match id attributes and useful resource attributes in your insurance policies. After this launch, we adopted up with help for the usage of ABAC together with AWS SSO and Cognito.
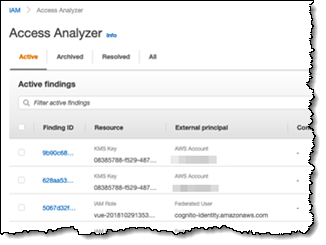 December 2019 – We launched IAM Entry Analyzer to research your insurance policies and decide which sources could be accessed publicly or from different accounts.
December 2019 – We launched IAM Entry Analyzer to research your insurance policies and decide which sources could be accessed publicly or from different accounts.
March 2021 – We added coverage validation (over 100 coverage checks) and actionable suggestions to IAM Entry Analyzer so as to assist you to assemble IAM insurance policies and SCPs that reap the benefits of time-tested AWS greatest practices.
April 2021 – We made it potential so that you can generate least-privilege IAM coverage templates based mostly on entry exercise.
Then and Now
Within the early days, a typical buyer may use IAM to manage entry to a handful of S3 buckets, EC2 cases, and SQS queues, all in a single AWS account. Nowadays, a few of our clients use IAM to manage entry to billions of objects that span a number of AWS accounts!
As a result of each name to an AWS API should name upon IAM to test permissions, the IAM crew has targeted on availability and scalability from the get-go. Again in 2011 the “can the caller do that?” operate dealt with a few thousand requests per second. Right now, as new companies proceed to seem and the AWS buyer base continues to climb, this operate now handles greater than 400 million API calls per second worldwide.
As you’ll be able to see from my abstract, IAM has come fairly a good distance from its easy but highly effective beginnings only a decade in the past. Whereas a lot of what was true a decade in the past stays true at present, I wish to name your consideration to a couple greatest practices which have advanced over time.
A number of Accounts – Initially, clients typically used a single AWS account and a number of customers. Right now, so as to accommodate a number of enterprise items and workloads, we suggest the usage of AWS Organizations and a number of accounts. Even when your AWS utilization is comparatively easy and simple at first, your utilization is more likely to develop in scale and complexity, and it’s at all times good to plan for this up entrance. To be taught extra, learn Establishing Your Finest Follow AWS Surroundings.
Customers & SSO – In a associated vein, we suggest that you simply use AWS SSO to create and handle customers centrally, after which grant them entry to a number of AWS accounts. To be taught extra, learn the AWS Single Signal-On Person Information.
Completely happy Birthday, IAM
Consistent with our well-known penchant for Buyer Obsession, your suggestions is at all times welcome! What new IAM options and capabilities would you prefer to see within the decade to return? Go away us a remark and I’ll guarantee that the crew sees it.
And with that, glad 10th birthday, IAM!
— Jeff;
[ad_2]
Source link






