[ad_1]

|
With Amazon CloudFront, you’ll be able to securely ship information, movies, purposes, and APIs to your prospects globally with low latency and excessive switch speeds. To supply a personalized expertise and the bottom potential latency, many trendy purposes execute some type of logic on the edge. The use circumstances for making use of logic on the edge will be grouped collectively in two important classes:
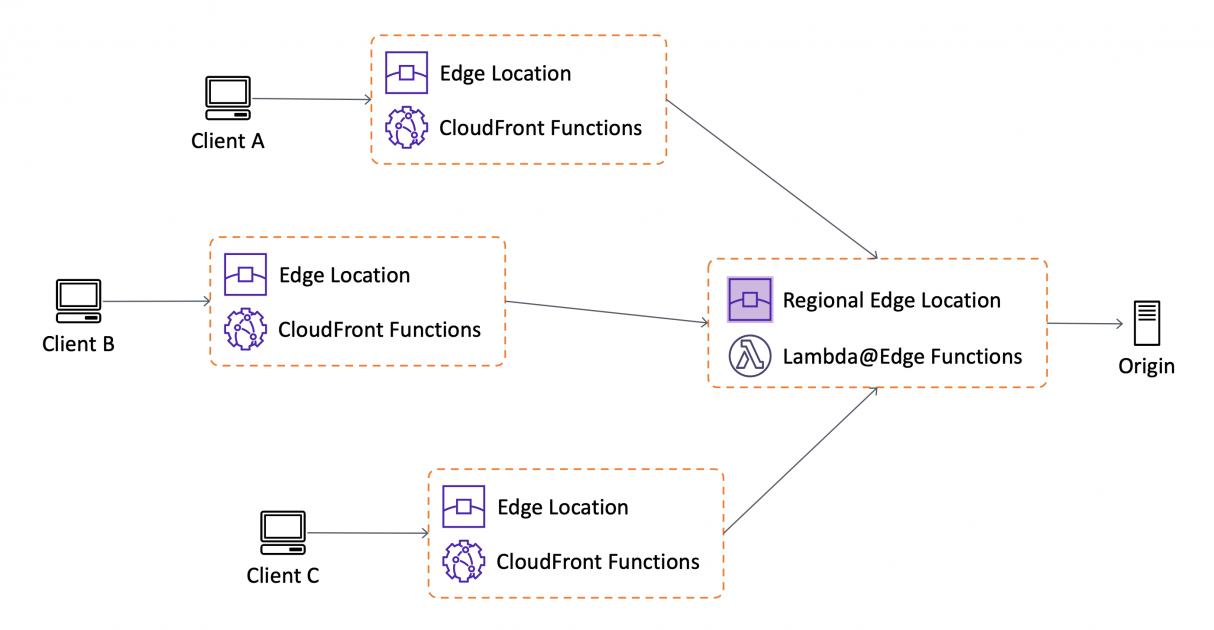
- First are the complicated, compute-heavy operations which might be executed when objects usually are not within the cache. We launched Lambda@Edge in 2017 to supply a completely programmable, serverless edge computing setting for implementing all kinds of complicated customizations. Lambda@Edge capabilities are executed in a regional edge cache (normally within the AWS area closest to the CloudFront edge location reached by the consumer). For instance, whenever you’re streaming video or audio, you should use Lambda@Edge to create and serve the precise segments on-the-fly decreasing the necessity for origin scalability. One other frequent use case is to make use of Lambda@Edge and Amazon DynamoDB to translate shortened, user-friendly URLs to full URL touchdown pages.
- The second class of use circumstances are easy HTTP(s) request/response manipulations that may be executed by very short-lived capabilities. For these use circumstances, you want a versatile programming expertise with the efficiency, scale, and cost-effectiveness that allow you to execute them on each request.
That can assist you with this second class of use circumstances, I’m completely satisfied to announce the provision of CloudFront Capabilities, a brand new serverless scripting platform that permits you to run light-weight JavaScript code on the 218+ CloudFront edge areas at roughly 1/sixth the worth of Lambda@Edge.

CloudFront Capabilities are perfect for light-weight processing of internet requests, for instance:
- Cache-key manipulations and normalization: Rework HTTP request attributes (reminiscent of URL, headers, cookies, and question strings) to assemble the cache-key, which is the distinctive identifier for objects in cache and is used to find out whether or not an object is already cached. For instance, you might cache primarily based on a header that incorporates the top person’s machine sort, creating two completely different variations of the content material for cell and desktop customers. By reworking the request attributes, you can even normalize a number of requests to a single cache-key entry and considerably enhance your cache-hit ratio.
- URL rewrites and redirects: Generate a response to redirect requests to a unique URL. For instance, redirect a non-authenticated person from a restricted web page to a login kind. URL rewrites can be used for A/B testing.
- HTTP header manipulation: View, add, modify, or delete any of the request/response headers. As an illustration, add HTTP Strict Transport Safety (HSTS) headers to your response, or copy the consumer IP handle into a brand new HTTP header in order that it’s forwarded to the origin with the request.
- Entry authorization: Implement entry management and authorization for the content material delivered by means of CloudFront by creating and validating user-generated tokens, reminiscent of HMAC tokens or JSON internet tokens (JWT), to permit/deny requests.
To provide the efficiency and scale that trendy purposes require, CloudFront Capabilities makes use of a brand new process-based isolation mannequin as an alternative of digital machine (VM)-based isolation as utilized by AWS Lambda and Lambda@Edge. To do this, we needed to implement some restrictions, reminiscent of avoiding community and file system entry. Additionally, capabilities run for lower than one millisecond. On this method, they will deal with tens of millions of requests per second whereas providing you with nice efficiency on each operate execution. Capabilities add nearly no perceptible impression to total content material supply community (CDN) efficiency.
Just like Lambda@Edge, CloudFront Capabilities runs your code in response to occasions generated by CloudFront. Extra particularly, CloudFront Capabilities will be triggered after CloudFront receives a request from a viewer (viewer request) and earlier than CloudFront forwards the response to the viewer (viewer response).
Lambda@Edge can be triggered earlier than CloudFront forwards the request to the origin (origin request) and after CloudFront receives the response from the origin (origin response). You need to use CloudFront Capabilities and Lambda@Edge collectively, relying on whether or not it’s essential manipulate content material earlier than, or after, being cached.

For those who want a number of the capabilities of Lambda@Edge that aren’t out there with CloudFront Capabilities, reminiscent of community entry or an extended execution time, you’ll be able to nonetheless use Lambda@Edge earlier than and after content material is cached by CloudFront.

That can assist you perceive the distinction between CloudFront Capabilities and Lambda@Edge, right here’s a fast comparability:
| CloudFront Capabilities | Lambda@Edge | |
| Runtime assist | JavaScript (ECMAScript 5.1 compliant) |
Node.js, Python |
| Execution location | 218+ CloudFront Edge Places |
13 CloudFront Regional Edge Caches |
| CloudFront triggers supported | Viewer request Viewer response |
Viewer request Viewer response Origin request Origin response |
| Most execution time | Lower than 1 millisecond | 5 seconds (viewer triggers) 30 seconds (origin triggers) |
| Most reminiscence | 2MB | 128MB (viewer triggers) 10GB (origin triggers) |
| Whole package deal dimension | 10 KB | 1 MB (viewer triggers) 50 MB (origin triggers) |
| Community entry | No | Sure |
| File system entry | No | Sure |
| Entry to the request physique | No | Sure |
| Pricing | Free tier out there; charged per request |
No free tier; charged per request and performance period |
Let’s see how this works in follow.
Utilizing CloudFront Capabilities From the Console
I need to customise the content material of my web site relying on the nation of origin of the viewers. To take action, I take advantage of a CloudFront distribution that I created utilizing an S3 bucket as origin. Then, I create a cache coverage to incorporate the CloudFront-Viewer-Nation header (that incorporates the two-letter nation code of the viewer’s nation) within the cache key. CloudFront Capabilities can see CloudFront-generated headers (just like the CloudFront geolocation or machine detection headers) provided that they’re included in an origin coverage or cache key coverage.
Within the CloudFront console, I choose Capabilities on the left bar after which Create operate. I give the operate a reputation and Proceed.

From right here, I can observe the lifecycle of my operate with these steps:
- Construct the operate by offering the code.
- Take a look at the operate with a pattern payload.
- Publish the operate from the event stage to the reside stage.
- Affiliate the operate with a number of CloudFront distributions.

1. Within the Construct tab, I can entry two levels for every operate: a Improvement stage for checks, and a Reside stage that can be utilized by a number of CloudFront distributions. With the event stage chosen, I sort the code of my operate and Save:
operate handler(occasion) {
var request = occasion.request;
var supported_countries = ['de', 'it', 'fr'];
if (request.uri.substr(three,1) != '/') {
var headers = request.headers;
var newUri;
if (headers['cloudfront-viewer-country'])
if (newUri === undefined)
var defaultCountryCode="en";
newUri = '/' + defaultCountryCode + request.uri;
var response =
return response;
}
return request;
}The operate appears on the content material of the CloudFront-Viewer-Nation header set by CloudFront. If it incorporates one of many supported nations, and the URL doesn’t already include a rustic prefix, it provides the nation at first of the URL path. In any other case, it lets the request go by means of with out modifications.
2. Within the Take a look at tab, I choose the occasion sort (Viewer Request), the Stage (Improvement, for now) and a pattern occasion.

Beneath, I can customise the Enter occasion by choosing the HTTP methodology, after which enhancing the trail of the URL, and optionally the consumer IP to make use of. I can even add customized headers, cookies, or question strings. In my case, I depart all of the default values and add the CloudFront-Viewer-Nation header with the worth of FR (for France). Optionally, as an alternative of utilizing the visible editor, I can customise the enter occasion by enhancing the JSON payload that’s handed to the operate.

I click on on the Take a look at button and take a look at the Output. As anticipated, the request is being redirected (HTTP standing code 302). Within the Response headers, I see that the location the place the request is being redirected begins with /fr/ to supply customized content material for viewers primarily based in France. If one thing doesn’t go as anticipated in my checks, I can take a look at the Perform Logs. I can even use console.log() in my code so as to add extra debugging data.

Within the Output, simply above the HTTP standing, I see the Compute utilization for this execution. Compute utilization is a quantity between zero and 100 that signifies the period of time that the operate took to run as a proportion of the utmost allowed time. In my case, a compute utilization of 21 implies that the operate accomplished in 21% of the utmost allowed time.
three. I run extra checks utilizing completely different configurations of URL and headers, then I transfer to the Publish tab to repeat the operate from the event stage to the reside stage. Now, the operate is able to be related to an present distribution.

four. Within the Affiliate tab, I choose the Distribution, the Occasion sort (Viewer Request or Viewer Response) and the Cache conduct (I solely have the Default cache conduct for my distribution). I click on Add affiliation and make sure within the dialog.

Now, I see the operate affiliation on the backside of the Affiliate tab.

To check this configuration from two completely different areas, I begin two Amazon Elastic Compute Cloud (EC2) situations, one within the US East (N. Virginia) Area and one within the Europe (Paris) Area. I join utilizing SSH and use cURL to get an object from the CloudFront distribution. Beforehand, I’ve uploaded two objects to the S3 bucket that’s used because the origin for the distribution: one, for patrons primarily based in France, utilizing the fr/ prefix, and one, for patrons not in a supported nation, utilizing the en/ prefix.
I listing the 2 objects utilizing the AWS Command Line Interface (CLI):
Within the EC2 occasion within the US East (N. Virginia) Area, I run this command to obtain the article:
Then I run the identical command within the Europe (Paris) Area:
As anticipated, I get completely different outcomes from the identical URL. I’m utilizing the -L possibility in order that cURL is following the redirect it receives. On this method, every command is executing two HTTP requests: the primary request receives the HTTP redirect from the CloudFront operate, the second request follows the redirect and isn’t modified by the operate as a result of it incorporates a customized path within the URL (/en/ or /fr/).
To see the precise location of the redirect and all HTTP response headers, I take advantage of cURL with the -i possibility. These are the response headers for the EC2 occasion operating within the US; the operate is executed at an edge location in Virginia:
And these are the response headers for the EC2 occasion operating in France; this time, the operate is executed in an edge location close to Paris:
Availability and Pricing
CloudFront Capabilities is offered at this time and you should use it with new and present distributions. You need to use CloudFront Capabilities with the AWS Administration Console, AWS Command Line Interface (CLI), AWS SDKs, and AWS CloudFormation. With CloudFront Capabilities, you pay by the variety of invocations. You will get began with CloudFront Capabilities at no cost as a part of the AWS Free Utilization Tier. For extra data, please see the CloudFront pricing web page.
Begin utilizing CloudFront Capabilities at this time so as to add customized logic on the edge to your purposes.
— Danilo
[ad_2]
Source link






