
[ad_1]

|
AWS Id and Entry Administration (IAM) is a vital and basic a part of AWS. You’ll be able to create IAM insurance policies and repair management insurance policies (SCPs) that outline the specified stage of entry to particular AWS providers and sources, after which connect the insurance policies to IAM principals (customers and roles), teams of customers, or to AWS sources. With the fine-grained management that you just get with IAM comes the duty to make use of it correctly, nearly all the time in search of to ascertain least privilege entry. The IAM tutorials will assist you to to study extra, and the IAM Entry Analyzer will assist you to to determine sources which can be shared with an exterior entity. We just lately launched an replace to IAM Entry Analyzer that permits you to Validate Entry to Your S3 Buckets Earlier than Deploying Permissions Adjustments.
New Coverage Validation
At the moment I’m blissful to announce that we’re including coverage validation to IAM Entry Analyzer. This highly effective new characteristic will assist you to to assemble IAM insurance policies and SCPs that benefit from time-tested AWS finest practices.
Designed to be used by builders and safety groups, validation takes place earlier than insurance policies are connected to IAM principals. Over 100 checks, every designed to designed to enhance your safety posture and that can assist you to simplify coverage administration at scale, are carried out. The findings from every test embody detailed data and concrete suggestions.
Validation is accessible from the JSON Coverage Editor within the IAM Console, in addition to from the command line (aws accessanalyzer validate-policy) and your personal code (ValidatePolicy). You should use the CLI and API choices to carry out programmatic validation as a part of your CI/CD workflows.
Within the IAM Console, coverage validation takes place in real-time everytime you create or edit a customer-managed coverage, with findings damaged down by severity; listed below are some examples:
Safety – Coverage components which can be overly permissive, and that could be a safety danger. This consists of use of iam:PassRole at the side of NotResource or with “*” (wildcard) because the useful resource:
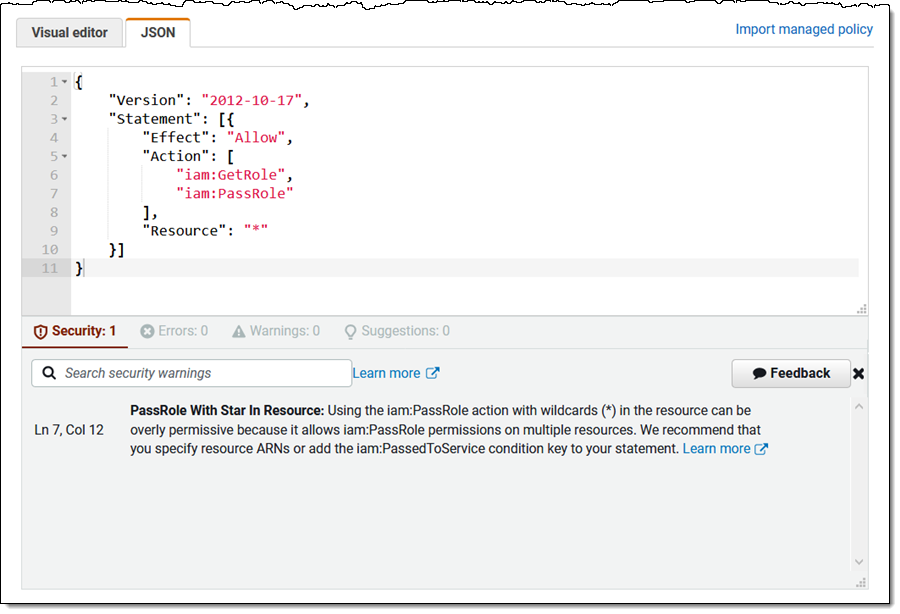
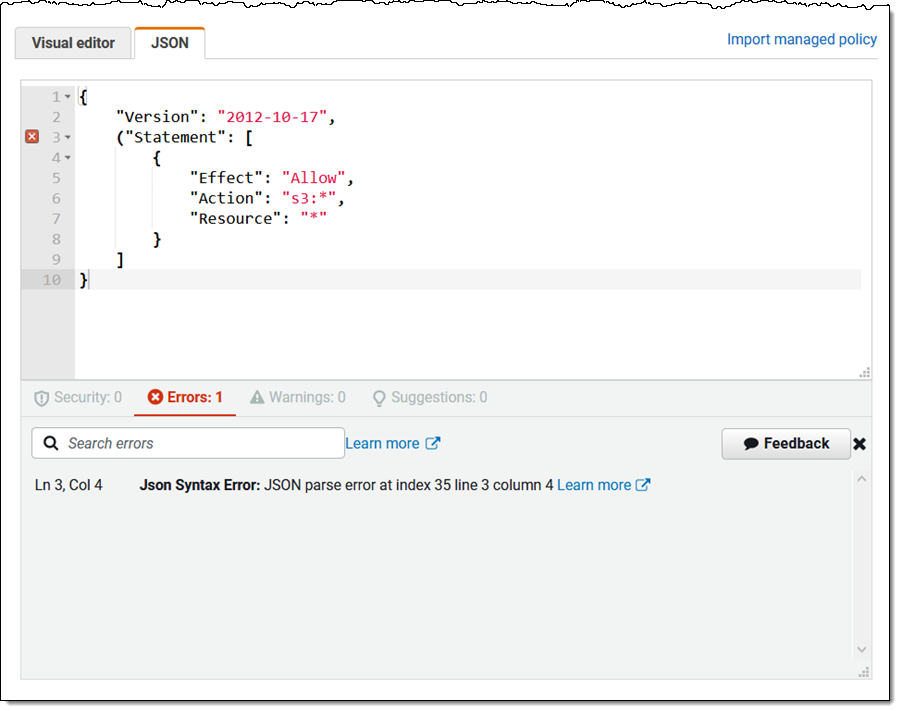
Error – Coverage components that cease the coverage from functioning. This consists of many kinds of syntax errors, lacking actions, invalid constructs, and so forth:
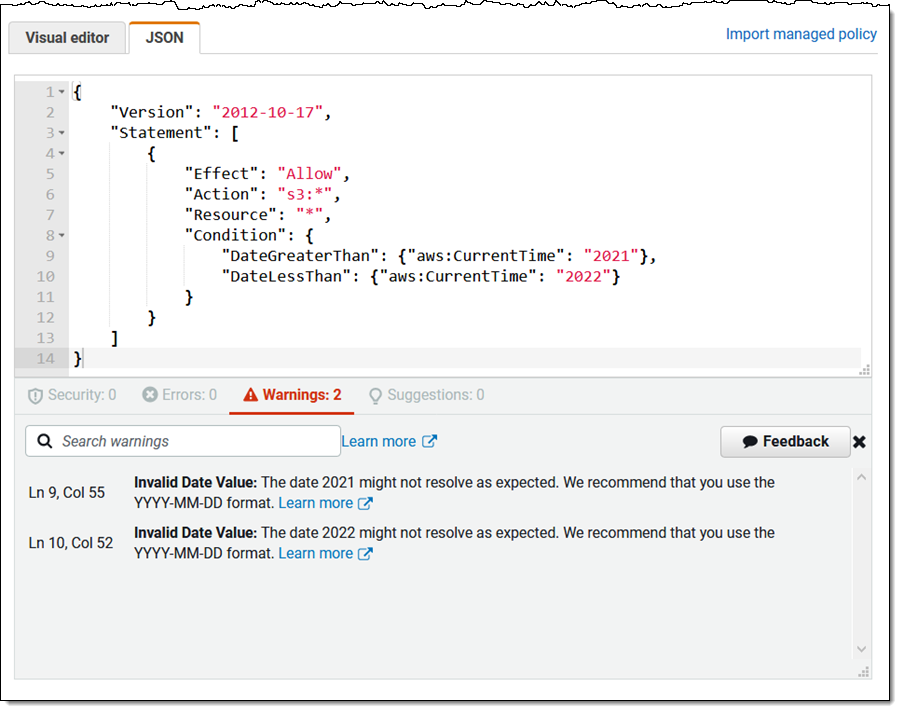
Warning – Coverage components that don’t conform to AWS finest practices, reminiscent of references to deprecated world situation keys or invalid customers, and using ambiguous dates:
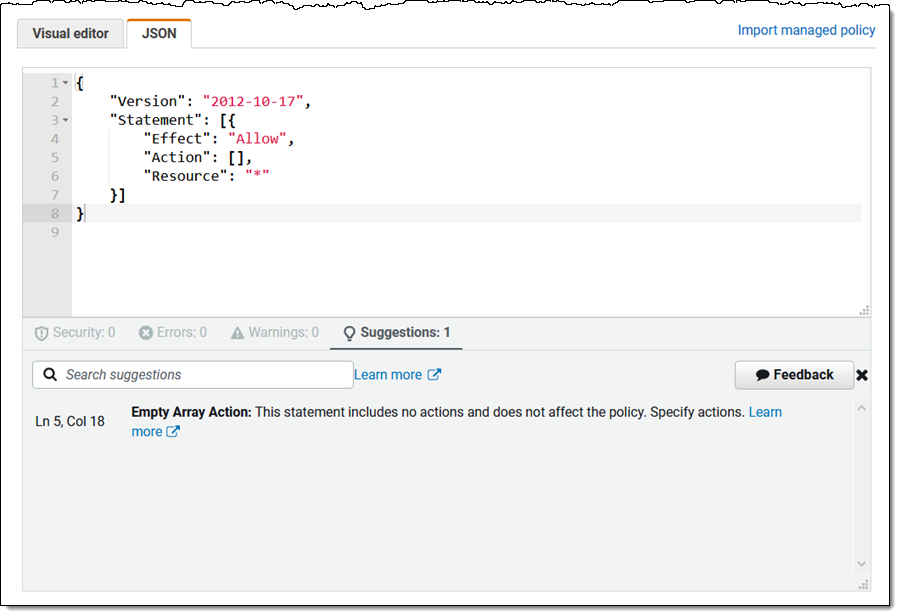
Suggestion – Coverage components which can be lacking, empty, or redundant:
Issues to Know
As I famous earlier, we’re launching with a set of over 100 checks. We’ve got plans so as to add extra over time, and welcome your options.
Within the Amazon spirit of consuming our personal Champagne, we routinely validate the Amazon-managed IAM insurance policies and fine-tune them when applicable. Once in a while we mark present managed insurance policies as deprecated, problem notifications to our clients through electronic mail, and make up to date replacements out there. To study extra about our course of, learn Deprecated AWS Managed Insurance policies.
As you might know, there are already a number of open supply coverage linters out there for AWS, together with the well-known Parliament from Duo Labs. Our clients instructed us that these instruments are helpful, however that they needed an AWS-native validation characteristic that was energetic whereas they have been enhancing insurance policies. A gaggle of builders on the IAM staff responded to this suggestions and carried out coverage validation from the bottom up.
You should use this characteristic now in all AWS areas at no cost.
— Jeff;
[ad_2]
Source link






