[ad_1] In some circumstances, when the usual output can’t be used for printing logs,...
Google Cloud
[ad_1] Monetary companies APIs are incessantly the goal of malicious bot assaults as a...
[ad_1] June noticed the in-person return of the RSA Convention in San Francisco, one...
[ad_1] Black Kite identifies vulnerabilities and assault patterns utilizing 400 safety controls and over...
[ad_1] Monitoring metrics ‘Reservation Complete Bytes’ offers details about the BI engine capability reservation...
[ad_1] IT networking conversations contain numerous phrases that could be unfamilair to many. Attempting...
[ad_1] Digital channels and on-demand banking have led prospects to count on immediate and...
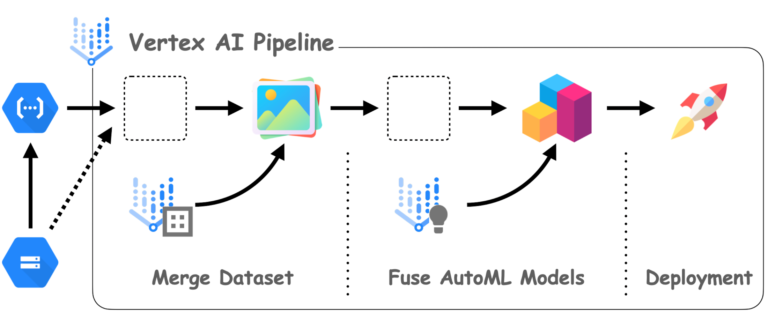
[ad_1] Determine 1 exhibits the general structure of this weblog. Let’s first go over...
[ad_1] Mercari is likely one of the most profitable market providers lately, with 5.three...
[ad_1] From product suggestions, to fraud detection, to route optimization, low latency predictions are...